CrowdStrike users to be wary of ongoing phishing scam
On Friday (19 July), the cybersecurity company CrowdStrike experienced a global outage that affected numerous organizations across the world, from financial institutions to airports.
The outage came from a defect in an update to CrowdStrike’s Falcon Sensor software, which many companies and government bodies use.
SingCert has now warned that there is an ongoing phishing scam targeting CrowdStrike users following the global outage.
Ongoing phishing scam targets CrowdStrike users
In a statement on Saturday (20 July), SingCert stated that the “phishing campaign” uses the global outage to target CrowdStrike users.
Scammers involved in the campaign may do the following to trick their victims:
- Send phishing emails posing as CrowdStrike support to customers
- Impersonate staff of the company in phone calls
- Pose as independent researchers
- Claim to have evidence that there is a link between the outage and a cyberattack and offer remediation insights
- Sell scripts purporting to automate recovery from the content update issue
SingCert has also identified a list of possible malicious domains associated with the campaign, the names of which are available here.
The organisation has urged system administrators to configure their firewall rules and block connections to these domains.
They can additionally use the following CrowdStrike Falcon LogScale query to hunt for the domains involved in the campaign.
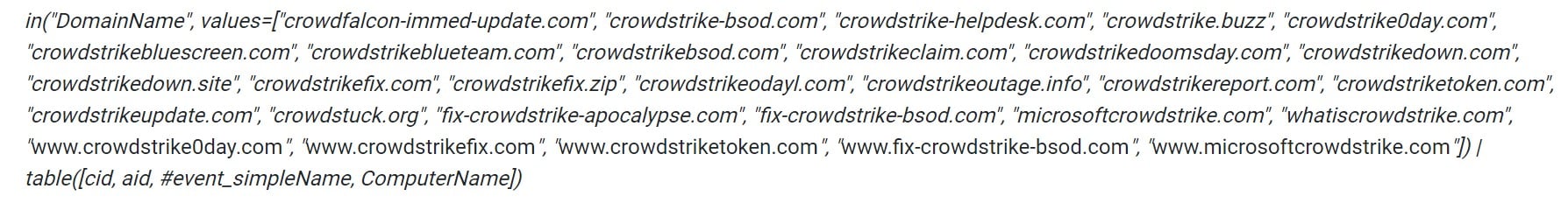
Source: SingCert
“It is advised that organisations ensure they are communicating with CrowdStrike representatives through official channels and adhere to technical guidance the CrowdStrike support teams have provided,” SingCert said.
Defect in update caused outage
The outage as a result of Crowdstrike’s update resulted in technical issues across the world, causing delays and cancellations of flights.
Changi Airport faced delays for over 40 flights, with numerous airlines resorting to manually checking in passengers for their trips.
By Saturday (20 July) morning, the airport updated that most check-in operations had been restored, with a few airlines still carrying out manual check-ins for their customers.
CrowdStrike Chief Executive Officer George Kurtz also shared on X that there had been a “defect” in a “single content update” for Windows hosts.
“The issue has been identified, isolated and a fix has been deployed,” he said.
Have news you must share? Get in touch with us via email at news@mustsharenews.com.
Featured image adapted from RNZ for illustration purposes only.