Microprocessor Security Flaws In Singapore Computing Devices
Practically the entire tech world was shook, when US security researchers highlighted massive security flaws due to bugs in major microprocessor brands on Wednesday (3 Jan).
Vulnerabilities that might allow hackers to steal sensitive information – like passwords, personal photos and emails – from virtually every computing device known to man.
 *immediately tries to reset password*
*immediately tries to reset password*
Source
Singapore Computer Emergency Response Team (SingCERT) has issued an advisory on Thursday (4 Jan) that devices in Singapore may be affected as well.
Here’s the lowdown on what you can do to save your device. We’ve also included what’s entirely out of your control.
A public Spectre and global Meltdown
SingCERT highlighted two “critical vulnerabilities”, aptly named Meltdown and Spectre, that will affect all of the following devices and services:
- Desktop Computers
- Smartphones
- Tablets
- Cloud Computing Services
The security vulnerabilities identified may “enable attackers to steal any data processed by the computer”.
Most importantly, SingCERT warned,
Successful exploit on vulnerable CPUs could allow attackers to read and access confidential information.
Confidential information like passwords, cryptographic keys, personal photos, emails or any other data on your PC or apps.
Malicious hackers can then use this data to “compromise computers or entire server networks”.
And how might they go about doing this?
Arguably the more serious flaw of the two, Meltdown “breaks the most fundamental isolation between user applications and the operating system”, according to Google.
This means hackers can easily access information from your Operating System’s (OS) memory, especially “sensitive data from other programmes”.
Meltdown affects mainly Intel processors due to the aggressive way they use ‘speculative execution’ – a way to optimise performance.
Spectre on the other hand, affects Intel, AMD and ARM processors. SingCERT added that it works by “trick(ing) applications into leaking its (their) data”.
Most personal devices are affected, but risk of hacking is low
Since this sounds pretty bad, everyone freaking out seems just about right.
The good news is that, everyday home users really shouldn’t panic too much.
Although your devices are probably also susceptible to these flaws, hackers won’t actively try to exploit your device just for your personal email password anyway.
Unless you’re privy to sensitive data on a daily basis, or if information security is in fact your day job.
What can regular users do to fix this?
Nothing. We’re doomed.
Just kidding. SingCERT recommends updating your firmware ASAP.
Users are reminded to ensure that all their devices are up-to-date with security patches and to activate their antivirus software.
You can do so by actively checking your vendors’ websites like Intel and Microsoft, and to update your OS to the latest version.
Anyhow, most OS providers like Windows, Linux and Apple are already rushing to fix the flaw.
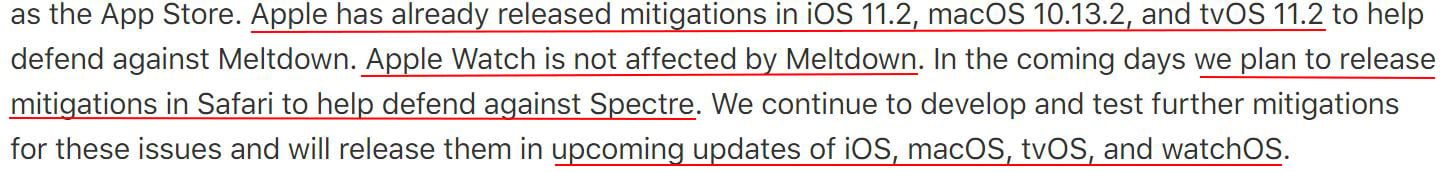
Apple’s kept a close Watch for security flaws
Apparently Apple users have less to worry as most of the issues from these security flaws have already been addressed in a previous patch.
They have since released a statement about a fix to be released “in the coming days” to defend against Spectre for their Safari browser.
Since Apple Watches are not affected by Meltdown, we guess Apple must have kept a close Watch for security flaws after all.
Google warned Intel about security flaws last year
Google said that they informed affected companies about the Spectre flaw as early as 1 Jun 2017, while Meltdown was reported before 28 Jul 2017.
In Intel’s defense, they claimed they were “aware of new security research” that when used maliciously could “improperly gather sensitive data from computing devices”.
They also clarified that “these exploits do not have the potential to corrupt, modify or delete data” and denied that these bugs were unique to Intel alone.
Bring on the security patches
Although AMD, ARM and Intel will eventually address the underlying “design issues”, the vulnerable systems are likely to remain in operation for decades to come.
In the meantime, our best bet is simply to wait patiently for software fixes to be released in Singapore. And to download them as soon as they’re out.
Now that you’ve been warned. Perhaps it’s only wise to let your friends and family know as well.
Featured image from SingCERT’s statement and SingCERT.

Drop us your email so you won't miss the latest news.